BCACTF 5.0!
Returning for its fifth consecutive year, this high school CTF hosted by the Bergen County Academies offers challenges across various difficulty levels, catering to everyone from beginners to seasoned CTF veterans.
I had the opportunity to participate in BCACTF 2024 as a member of my institute’s club, InfoSecIITR. Our team secured 7th Place globally. These writeups document the challenges I personally solved during the competition. The remaining challenges were tackled by my teammates.
Forensics
Mysterious Melody
Challenge Description
We have received a WAV file.
Solution
So, I opened the WAV file using Sonic Visualizer software. Initially, I was unsure of what to do after examining the Spectrogram. Then, I analyzed the melody range spectrogram and the peak frequency spectrogram.
1 | You can add the Spectrogram, Melody Range Spectrogram, and Peak Frequency Spectrogram from the Pane menu. |
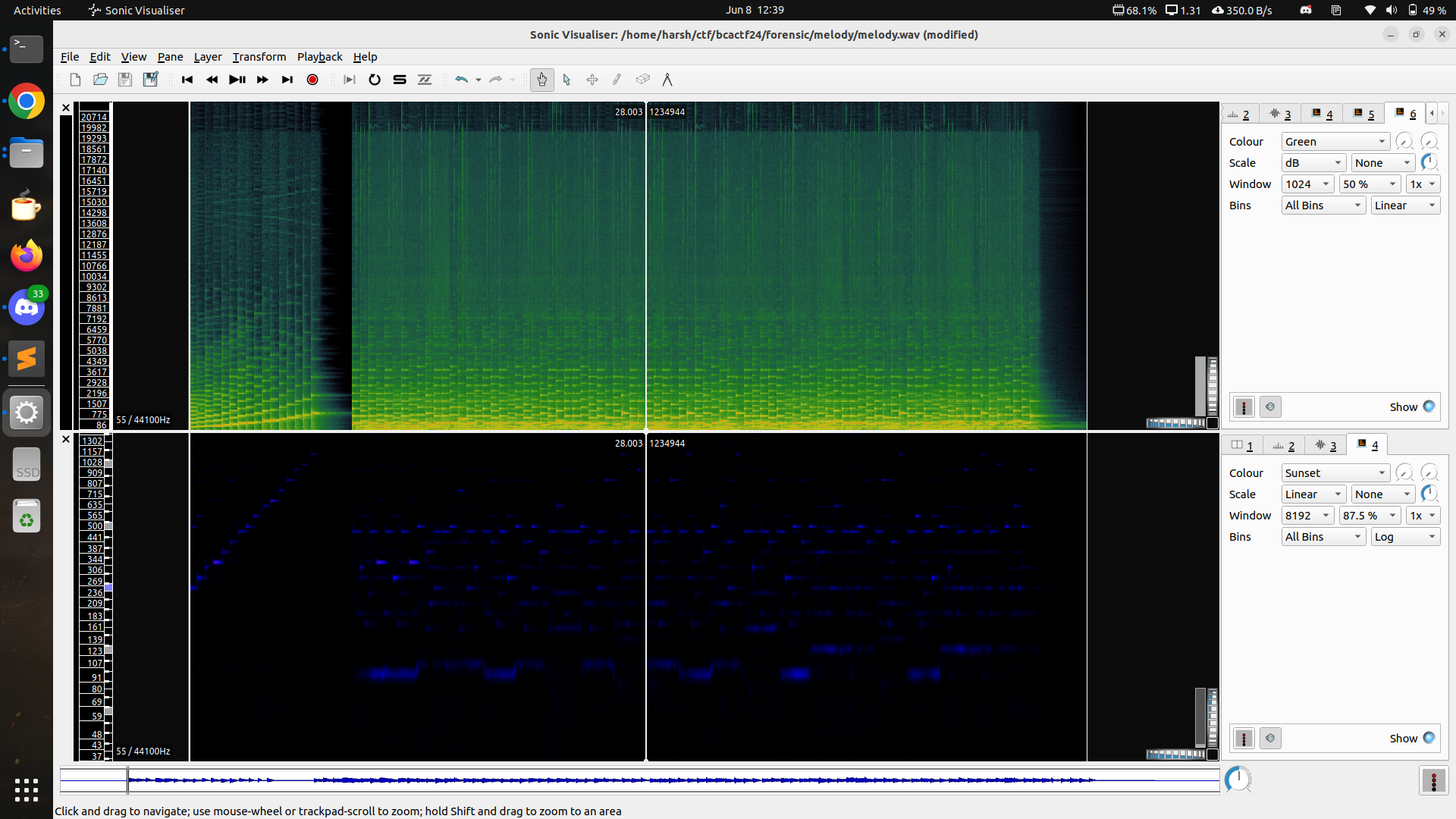
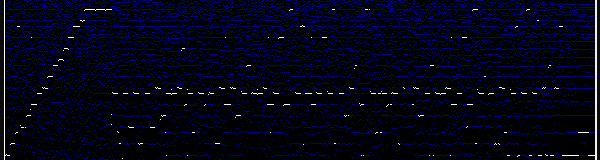
Where I noticed something unusual that resembled Morse code, but it wasn’t. On the left side, there were 16 increasing lines, which matched the base16 hint provided. The hex values for the start of the flag ‘bcactf{‘ corresponded to the highs and lows of the lines on the right side. This clue confirmed it was part of the flag, and from there, we decoded all the highs and lows.
6263616374667B62656175746966756C5F6D656C6F64795F62656175746966756C5F6861726D6F6E797D
Flag
bcactf{beautiful_melody_beautiful_harmony}
Static
Challenge Description
We have received a MP4 file and the MD5 of a file.
Solution
As the hints suggested, I began searching for the metadata.
1 | $ exiftool static.mp4 |
Two things seemed sus to me: the Compressor and the Encoder. I then checked the above link for StaticMaker and realized they provided a documentation file with information about the StaticMaker software.
1 | The StaticMaker ™ utility converts any binary file into a video, suitable for use in … some application somewhere, probably. |
WorkFlow:-
Extraction of Frames:
Utilizes FFmpeg to extract frames from the video.Extraction of Pixel Data:
Decodes the RGB channels of each frame.
Extracts 2 bits per pixel per channelReconstruction of Binary Data:
Combines the extracted bits into a single stream.
Reconstructs the original binary data by converting the bits back into bytes.
For Extraction of Frames:-
1 | $ ffmpeg -i static.mp4 frame_%04d.png |
Using ffmpeg, we extracted 72 frames in PNG format from the MP4 video.
Next, I wrote a Python script to accomplish steps 2 and 3.
1 | import hashlib |
The extracted bin matches the MD5 checksum provided in the description. As I began analyzing the file, I employed several tools. When I used binwalk, it indicated the presence of Zlib compressed data, which I then extracted.
1 | $ binwalk -e extracted_data.bin |
There are two approaches: one is quick and easy, while the other is little time-consuming.
This is the quick and easy method for lazy people like me to get the flag.
1 | g4rud4:~/Pictures/_extracted_data.bin.extracted$ ls |
Another one is to do it proper way:-
1 | $ zlib-flate -uncompress < 9E4A.zlib > output |
I began extracting the tar archive once we obtained it.
1 | $ tar -xf output |
We got some folders let’s check out
1 | $ tree . |
I began searching for the text files in the admin directories.
1 | ~/home/admin/Documents$ cat not_social_security_number.txt |
Hooray!!! We captured the flag just 3 minutes before the CTF ended. ;p
Flag
bcactf{imag3_PROc3sSINg_yaY_2ea104d700c1a8}

