I participated in Srdnlen CTF 2025, as a member of my institute’s club, InfoSecIITR. This writeup details the challenges of the forensics category.
Misc-Forensics
DFIR 1 - Malvent
Challenge Description
We have been notified of an attack in one of our machines. This is a real forensics investigation and you have to analyse the given evtx files and answer to the related questions. At the end you will get the flag when you answer everything correct.
Dfir 1 - Question 4: you have to find all the numbers separated by a comma related to insecure credential management (e.g., 1000, 2355, etc)
NOTE: This is a real malware. Do not execute nothing. Pay attention and be careful. Srdnlen denies every damage on your infrastructure.
This is a remote challenge, you can connect to the service with: nc dfir1.challs.srdnlen.it 1984
Author: slsanna
Attachments: al_evtx.zip
Solution
We received a series of DFIR Challenges from 1-4 and were provided with the al_evtx.zip file for the first challenge. To analyze these files, I used the Event Viewer tool.
Step 1: Initial Connection and Question 1
Let’s start by running the nc instance:
1 | $ nc dfir1.challs.srdnlen.it 1984 |
For this question, I started analyzing System logs. While checking the logs of the Source Service Control Manager, I noticed that a service with a random name had started, and the source of it was also a random filename, which seemed suspicious. This is shown below in the image:
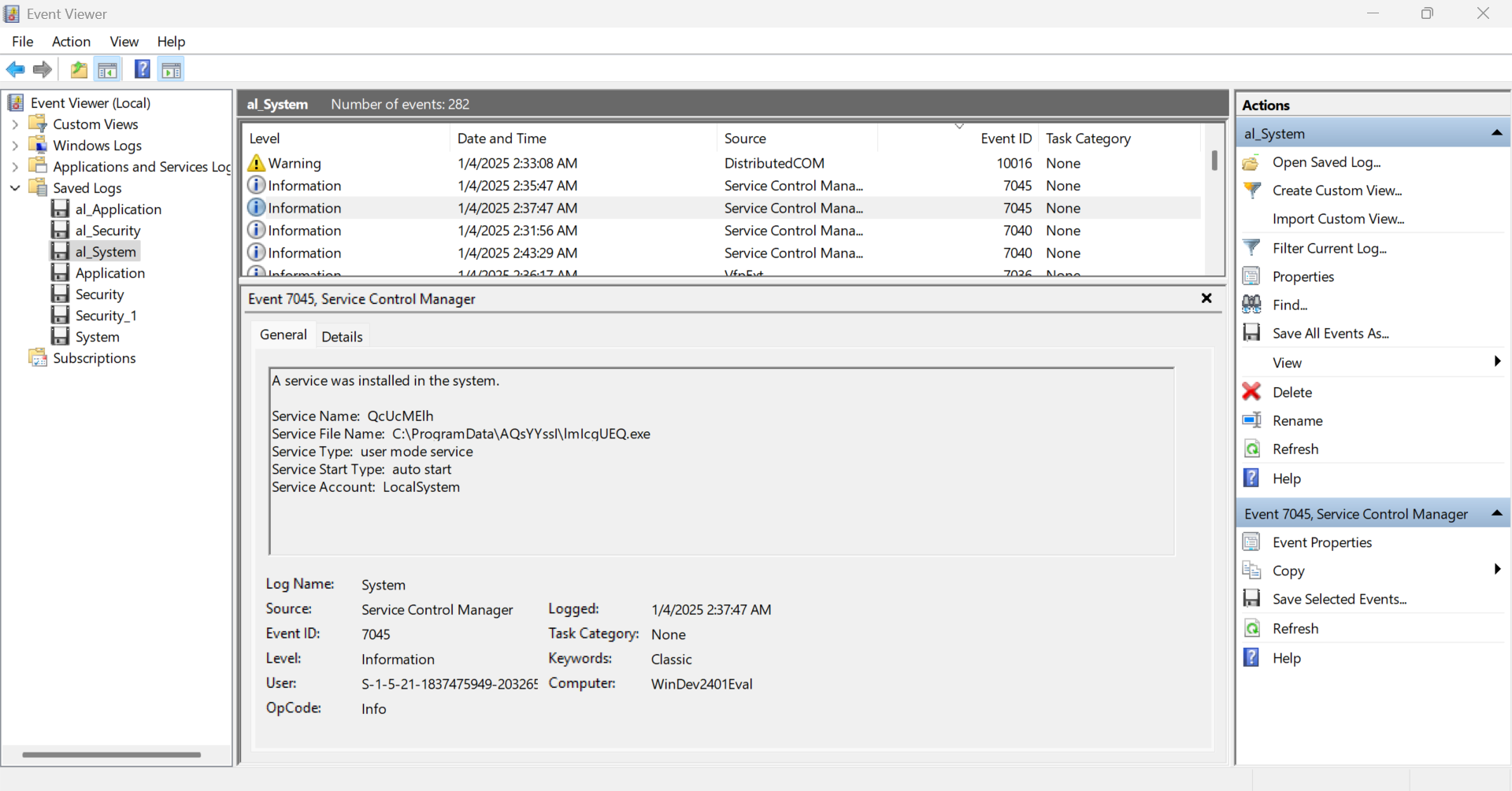
I submitted the name and found that it was the correct one.
1 | What is the name of the suspicious service installed? |
Using the same image above, I could answer the questions in Step 2 & 3.
1 | From which process it has been generated? Give also the extension |
Step 4: Finding Event IDs for Unsecured Data
I think this question was unclear, and the hint released later on, mentioned in the description, made it even more confusing. Because of this, we were unable to solve it, and many others were just analyzing the Security logs like us. Some of them brute-forced and found the correct one. :(
I got the answer to this question later from warlocksmurf. When analyzing the System logs, I came across the TPM Logs, which showed that the data could not be encrypted.
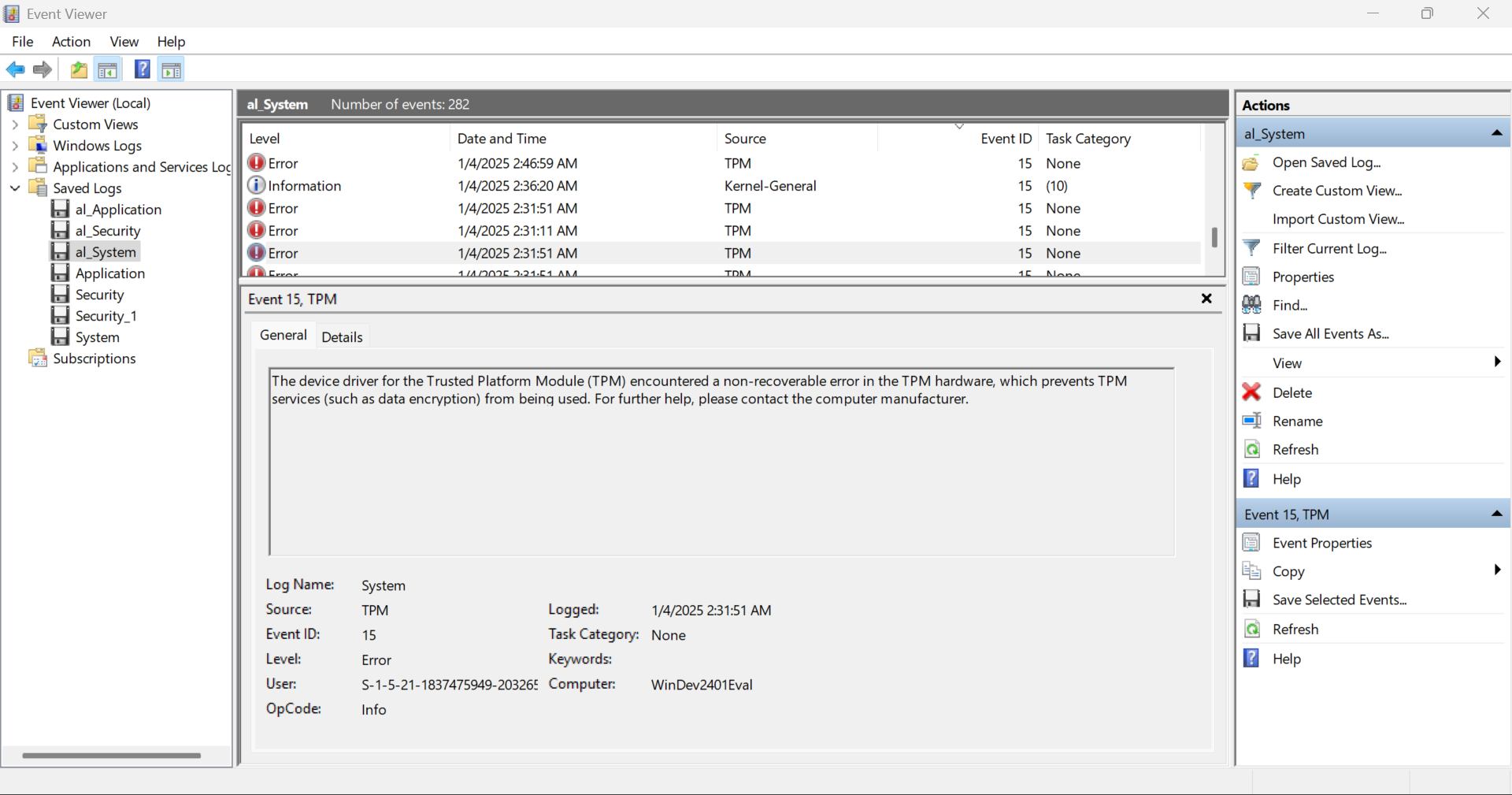
One of the event IDs is 15, and while finding the second event ID, I realized that event ID 18 contains the message: “This event triggers the Trusted Platform Module (TPM) provisioning/status check to run.” With this, we get both event IDs.
After this question, the rest were doable, and we could have completed this challenge during the competition.
1 | Give the events IDs corresponding to unsecured data (e.g. cryptography). If more than one put a comma (e.g. 1, 2) |
Step 5: Identifying the Event ID Related to Account Protection
While analyzing the System logs, I came across Event ID 16977 from the Source Directory-Services-SAM, which referenced the password.
1 | Which event ID is related to the state of the account protection? |
Step 6: Finding Compromised CLSIDs
For this question, search for “CLSID” in the System logs using Find. You will find two strings, as shown below:
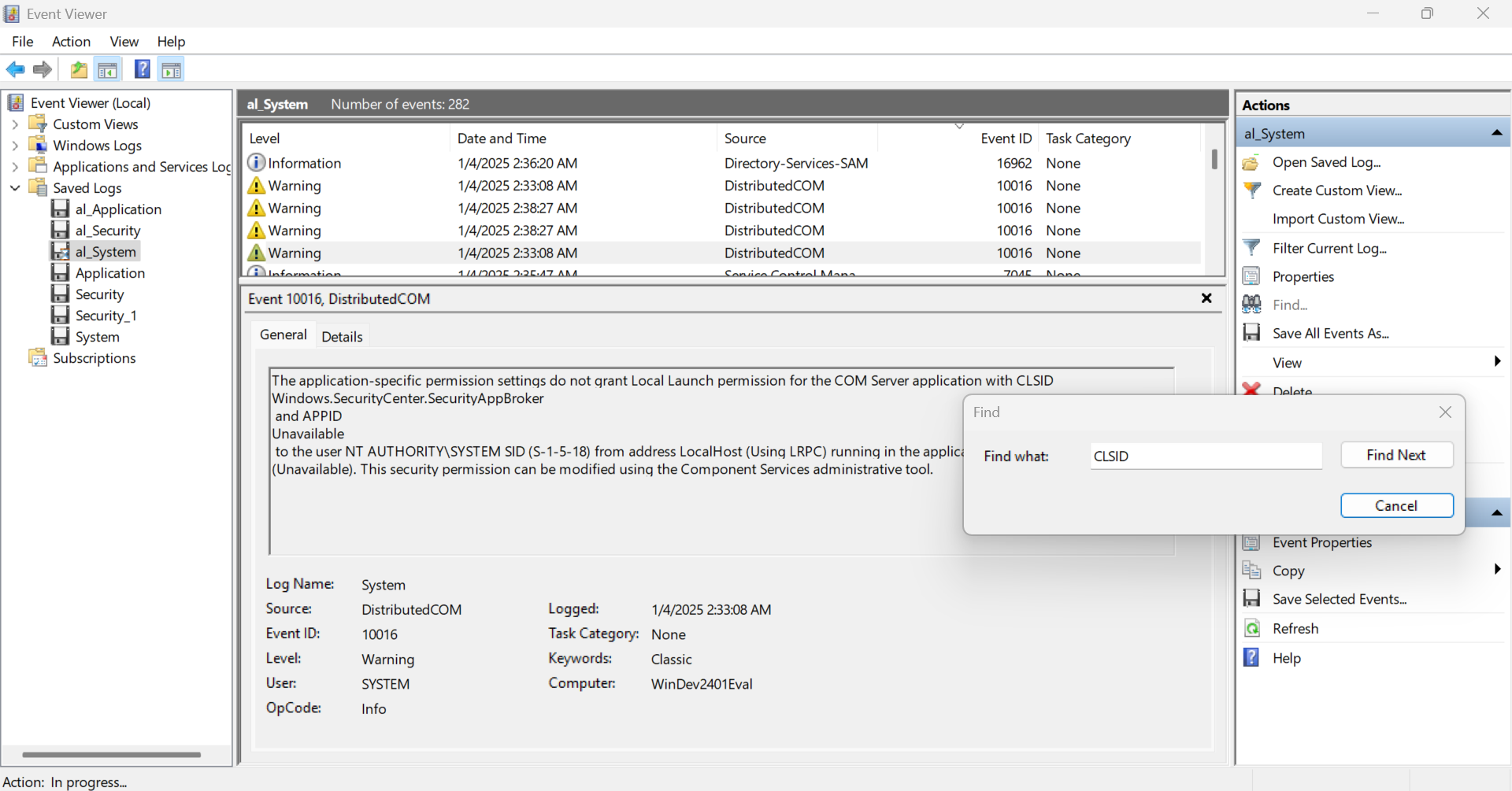
1 | Give the compromised CLSID stating that malicious code could be executed. If more than one, put a comma (e.g. str1, str2) |
Step 7: Determining the Port Number for Remote Control
For this question, I found RDP URLs in the System logs. I tried all the associated port numbers, and the correct one is shown below:
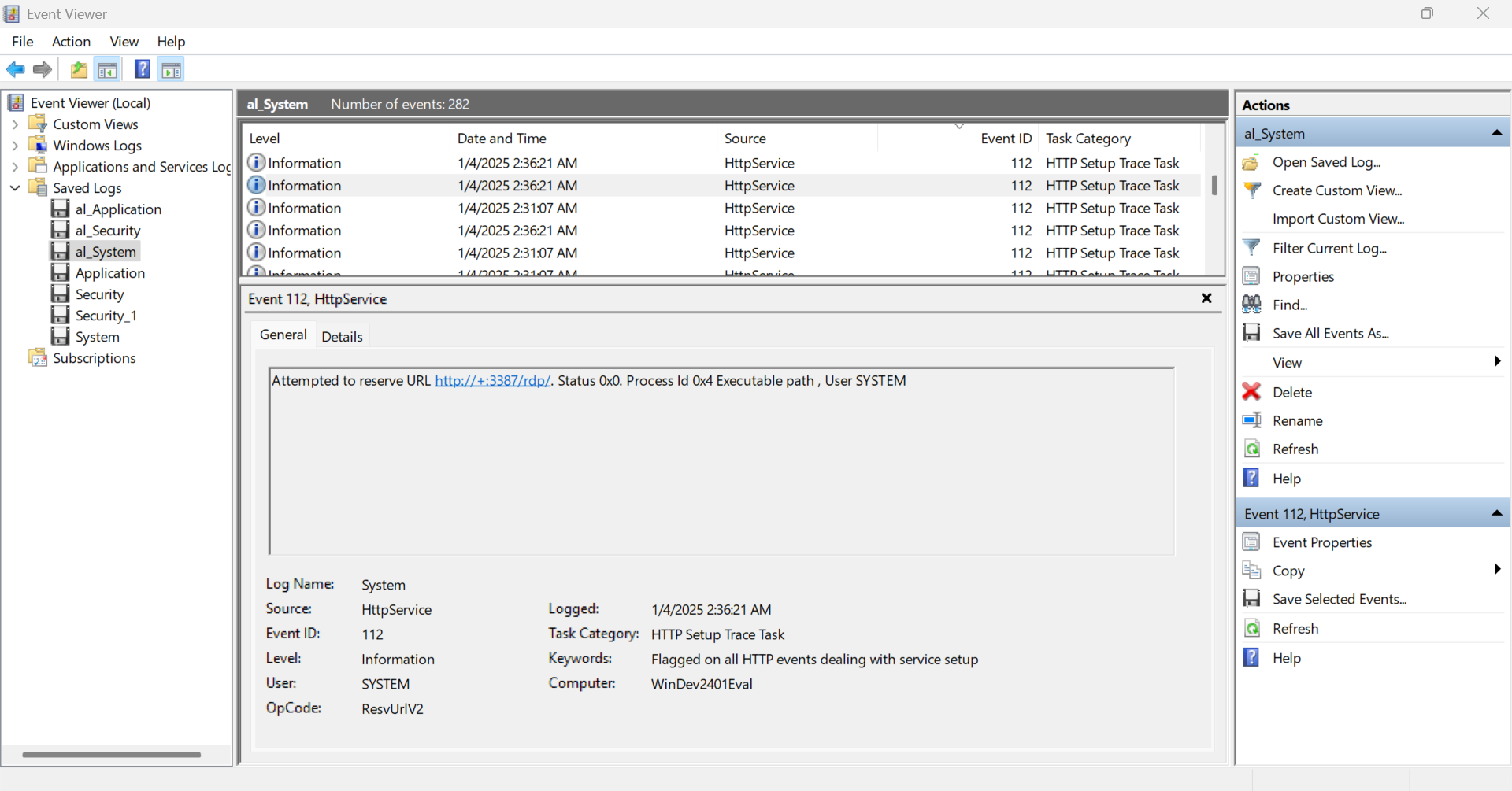
1 | What is the port number listening for remote control? |
Step 8: Locating the Event ID for the Manipulation
While analyzing the System logs, I found that Event ID 16 was associated with changes in Hives, which was the correct answer.
1 | Give the event ID related to the manipulation of specific data (e.g. registry key manipulation, deletion, creation, modification) |
Step 9: Finding the Malware-Affected Application
While analyzing the Application logs, I found an event with suspicious messages including Widgets.exe, which matched the question. This turned out to be the correct one.
1 | Give the application name whose corruption could depend from the malware. (First letter uppercase, add also the extension). |
Step 10: Checking Windows Defender Status
For this question, I found the result as shown below:
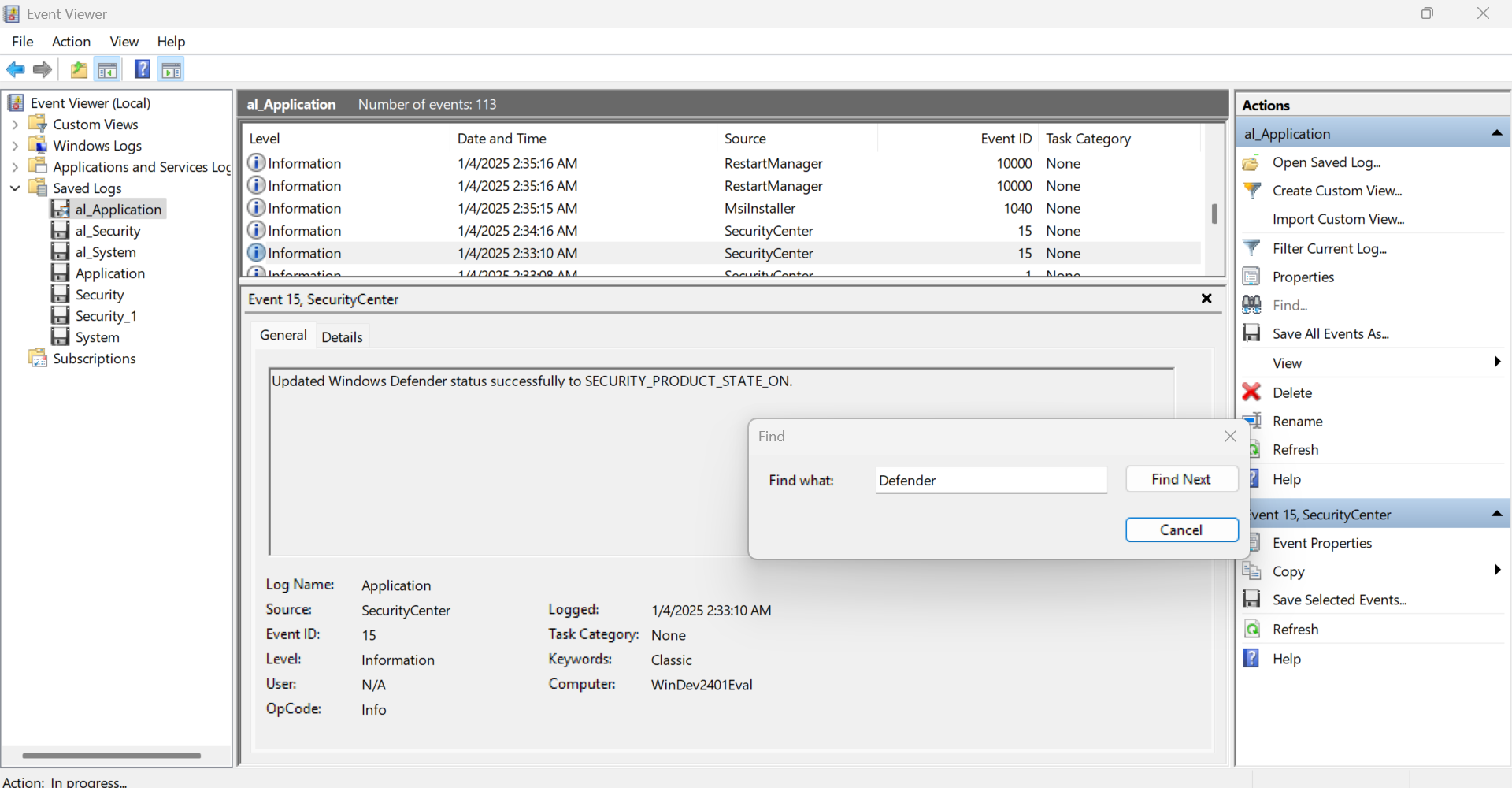
Windows Defender was on.
1 | Is Windows Defender on? |
Step 11: Identifying the Event ID Indicating Windows Defender Status
From the same image, you can see that the Event ID was 15.
1 | What is the event ID stating this? |
Step 12: Finding Event ID for Remote Desktop Mismanagement
You can find the answer in the Application logs. The message states:
“The winlogon notification subscriber
The event ID is 6003.
1 | Give the event ID related to the wrong management of different sessions and users in remote desktop |
Step 13: Locating the Event ID for Credential Access
I had memorized this Event ID earlier while analyzing the Security logs so much.
1 | Which event ID states that the malware could have read the credentials? |
We got our flag!!
Flag:
1 | srdnlen{DFIR1:evtx4system_mngmnt&malwan} |
DFIR 2 - Malnet
Challenge Description
We have been notified of an attack in one of our machines. This is a real forensics investigation and you have to analyse the given pcap file and answer to the related questions. At the end you will get the flag when you answer everything correct.
NOTE: This is a real malware. Do not execute nothing. Pay attention and be careful. Srdnlen denies every damage on your infrastructure.
This is a remote challenge, you can connect to the service with: nc dfir2.challs.srdnlen.it 1985
Author: slsanna
Attachments: capture_net.pcapng
Solution
I’d blooded this challenge :P. We were provided with a PCAPNG file and an nc interface to answer a series of questions. Let’s begin!
Step 1: Initial Connection and Question 1
I started by connecting to the challenge service to check the first question:
1 | $ nc dfir2.challs.srdnlen.it 1985 |
Using Wireshark, I exported all objects (File -> Export Objects) and identified the relevant files:
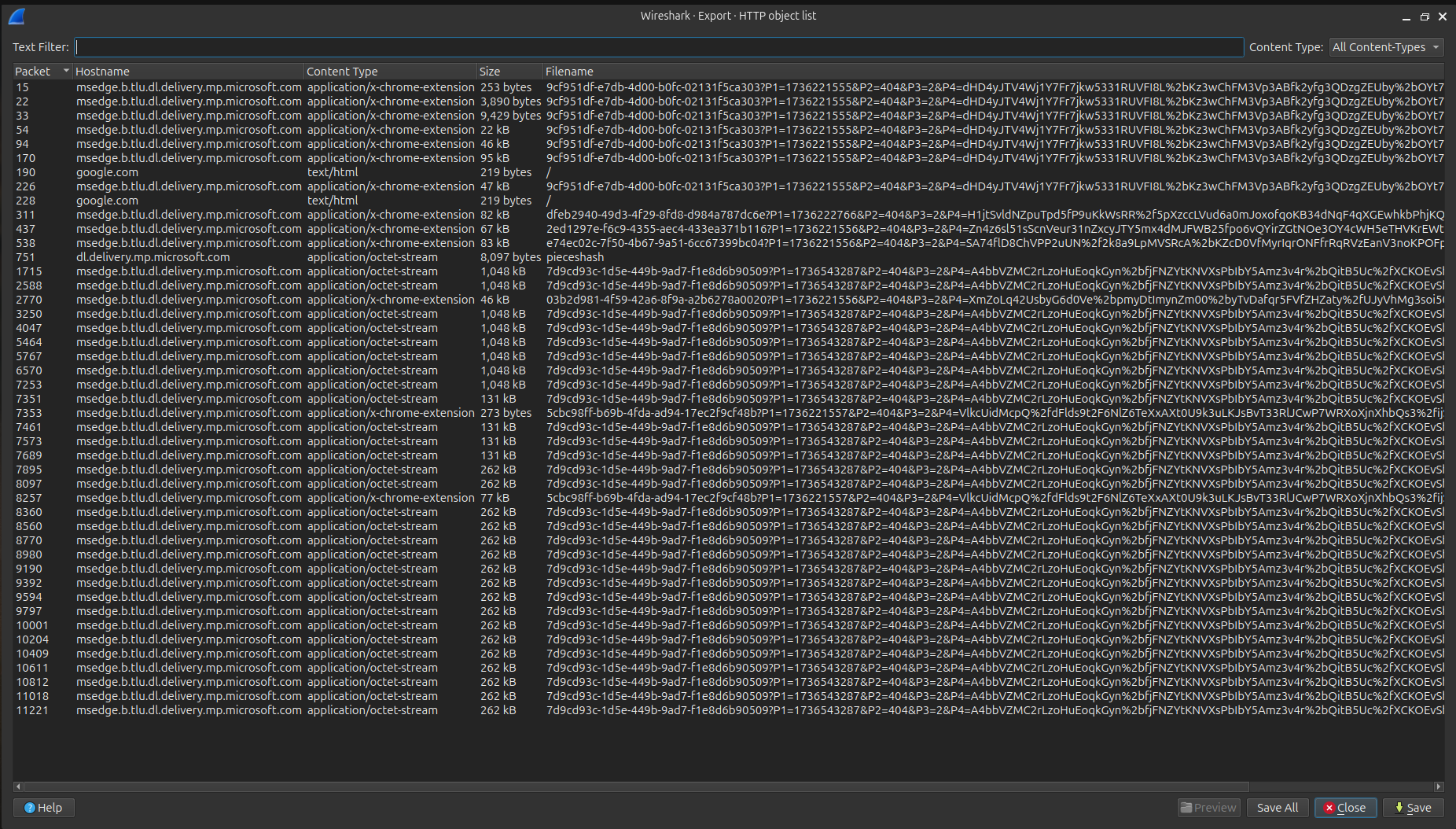
Here’s a snippet of the file types identified using the file command:
1 | $ file * |
The file marked with (2) was identified as PE32+. Initially, I checked the packet number of this file in the Export Objects list, but it did not match. To locate the desired packet, I applied a filter as shown below and found the correct packet, which was near the packet number listed in Export Objects.
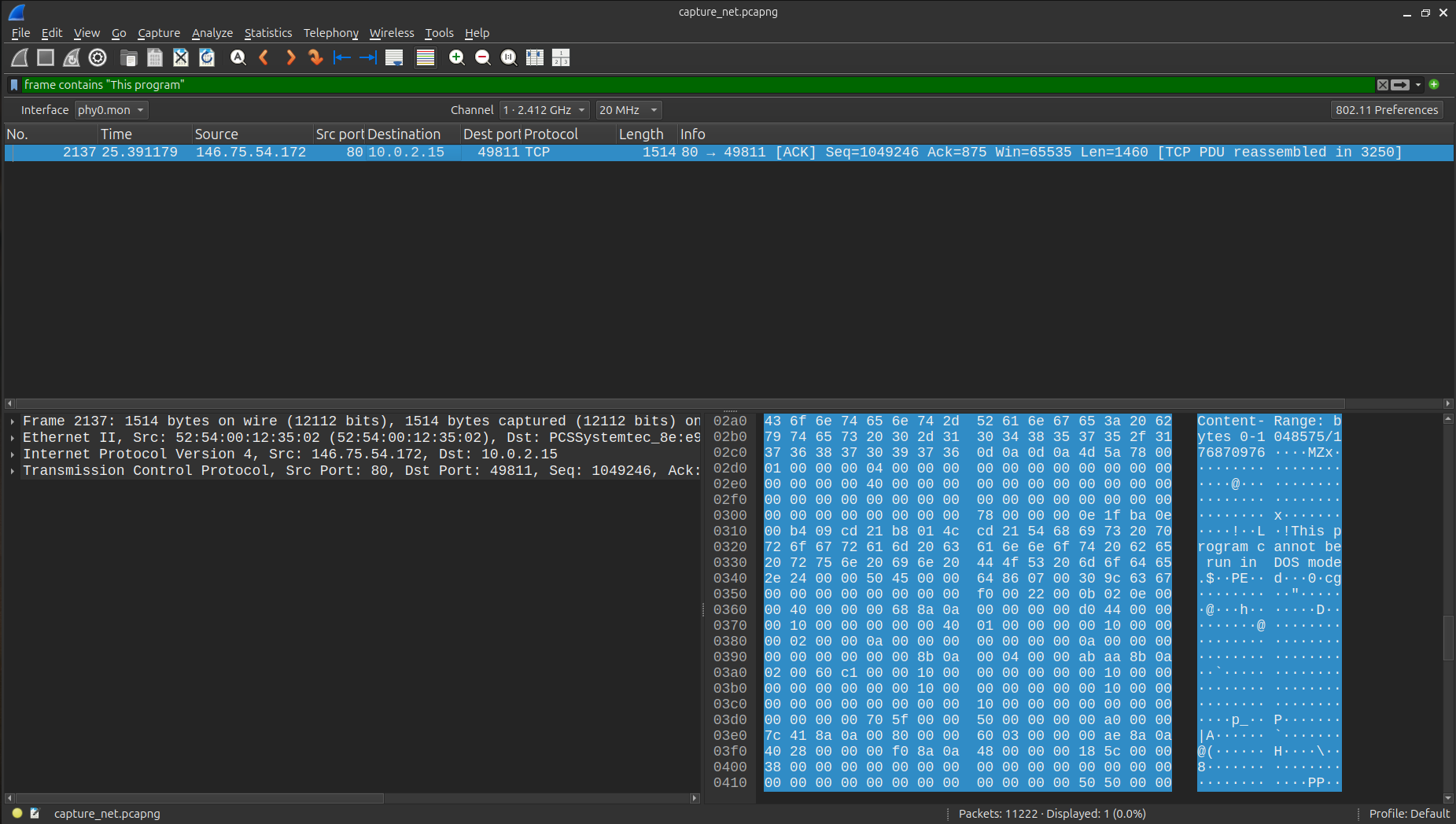
1 | Which packet contains the header of an executable file? |
Step 2: Determining Flow ID
To identify the Flow ID, I followed the TCP stream of Packet 2137 and determined the corresponding Flow ID: TCP 40.
1 | To which flow does it correspond? (PROTOCOLO FLOW_ID, e.g. HTTP 1) |
Step 3: Fragmentation
After saving the files locally, I found that the executable was fragmented into 29 parts (from 0 to 28).
1 | Into how many parts is the executable fragmented? Give the total number of files |
Step 4: Resource Name
Searching for the resource name in the packets revealed the following:
1 | What is the resource name accessed in the GET resource containing the executable file?. Give the complete name (e.g. /myfile/file1/this-is-the-file?A0=something&A1=other%3d%3d) |
Step 5: SHA256 Check
The SHA256 hash of the first part of the executable file (file (2)) was calculated as follows:
1 | $ sha256sum 7d9cd93c-1d5e-449b-9ad7-f1e8d6b90509%3fP1/=1736543287/&P2/=404/&P3/=2/&P4/=A4bbVZMC2rLzoHuEoqkGyn%2bfjFNZYtKNVXsPbIbY5Amz3v4r%2bQitB5Uc%2fXCKOEvShr8HAJPOsSVdpx2t0DGgKQ%3d%3d/(2/) |
1 | What is the sha256 of the first part of the executable file? |
Step 6 - Corresponding Extracted File Enumeration
Using the Wireshark export naming convention, the file corresponds to the index (2).
1 | To which of the extracted files does it correspond? As done by Wireshark, use the enumeration starting from 0 |
Step 7 - SHA-256 of the Reconstructed File
This was the trickiest question. As usual, I first attempted to reconstruct the 7d9cd93c-1d5e-449b-9ad7-f1e8d6b90509 file using the pieces numbered (0) to (28). However, the reconstructed file did not match the full size specified in the packet, which was 176,870,976 bytes. This prompted me to explore other sources for the hash. It occurred to me that we had also received a piecehash file, which might be useful.
The content of the piecehash file was as follows:
1 | {"MajorVersion":1,"MinorVersion":0,"HashOfHashes":"JvZyinMn7LiBqNeYmy7JPeu8Kn4chEzksqZUnwB2Pg4=","ContentLength":176870976,"PieceSize":1048576,"Pieces":["tWsO5K+PQ5VFXtT4Oy0lSYREyTn8931J7J7IPGiYPlI=","VXw6j5l8k7XNgyfLxfWGKbogZJOn/H9QjwKf8rKKgu0=","q2tg5LDXyy0r0B1aSW+cSfV73UedLIbMTQZ+V+UvlCs=",".... |
This file contained the HashOfHashes as well as 167 piece hashes. Since we already knew the size of the main file, which was also mentioned in this file, I hypothesized that the HashOfHashes could be the hash of the main file. I decoded the HashOfHashes and converted it to hexadecimal. Upon verification, it turned out to be the desired hash.
1 | What is the sha256sum of the reconstJust follow the packet and you will get the answer for the above question and also for after one.ructed file? |
Step 8 - Number of Non-Corrupted Chrome Extensions
Among the exported objects, six were Chrome extensions. Using the file command, I identified that one file did not display as a Google Chrome extension, version 3, indicating it was corrupted. Thus, five extensions were not corrupted.
1 | How many downloaded chrome extensions are not corrupted? |
Step 9 - Packet Related to Cryptomining
I applied the filter frame contains "cryptomin" in Wireshark and identified the relevant packet as:
1 | Which packet is related to cryptomining? |
Step 10 - Corresponding Flow for Cryptomining Packet
Following the TCP stream of packet 290 revealed the flow ID:
1 | To which flow does it correspond? (PROTOCOLO FLOW_ID, e.g. UDP 0) |
Step 11 - Resource Name for Cryptomining
The resource name associated with the packet was:
1 | What is the resource name? Give the complete name (e.g. /myfile/file1/this-is-the-file?A0=something&A1=other%3d%3d) |
Step 12 - SHA-256 of the Cryptomining File
To verify the cryptomining file, I exported it using Wireshark’s “Export Objects” feature and calculated its SHA-256 hash using the sha256sum command:
1 | Give the sha256 of the file related to cryptocurrency. |
Completed the challenge!
Flag:
1 | srdnlen{DFIR2:network_analysis_R34L_malware} |
DFIR 3 - RAMsomwhere
Challenge Description
We have been notified of an attack in one of our machines. This is a real forensics investigation and you have to analyse the given elf file and answer to the related questions. At the end you will get the flag when you answer everything correct.
For questions related to finding something network related “not present in the pcap” - we are referring to the pcap of DFIR2 - MalNet.
You can download the file from this link: https://tinyurl.com/srdnlenCTF24-dfir3
NOTE: This is a real malware. Do not execute nothing. Pay attention and be careful. Srdnlen denies every damage on your infrastructure.
This is a remote challenge, you can connect to the service with: nc dfir3.challs.srdnlen.it 1986
Author: slsanna
Solution
I received a memory capture ELF file and an nc instance. Let’s start:
1 | $ nc dfir3.challs.srdnlen.it 1986 |
Step 1: Finding the PID from EVTX Analysis
To analyze the memory file, I used Volatility3 to identify the PID of the process found in the EVTX analysis. The process in question was lmIcgUEQ.exe. The following steps were performed:
1 | $ python3 vol.py -f ~/Downloads/capture_ram.elf windows.pslist |
The desired PID is 2240.
1 | What is the PID of the process found in the evtx analysis? |
Step 2: Identifying the IP Not Found in the PCAP File
To answer this, I extracted all IPs from both the memory and PCAP file and identified the unique one:
1 | IPs in memory but not in PCAP: |
127.0.0.1 found to be the desired one.
1 | Which IP does not compare in the given pcap file? |
Step 3: Identifying the Chrome Extension in PCAP but Not in RAM
I first extracted all manifest.json files from Chrome extensions in RAM:
1 | $ python3 vol.py -f capture_ram.elf windows.filescan | grep -i chrome |
Repeat the above step, and the .dat file you get is the manifest.json of the Chrome extension. Then, I went on checking the Chrome extension files we extracted from the PCAPng.
After unzipping the Chrome extension file, you will find the manifest.json:
1 | $ unzip '2ed1297e-f6c9-4355-aec4-433ea371b116%3fP1=1736221556&P2=404&P3=2&P4=Zn4z6sl51sScnVeur31nZxcyJTY5mx4dMJFWB25fpo6vQYirZGtNOe3OY4cWH5eTHVKrEWtal87QWFUtShW2hg%3d%3d' |
The above chrome extension was not present in the RAM.
1 | What is the name in the manifest of the chrome extension found in the pcap and not in the RAM? |
Step 4: Finding Suspicious Processes
By reviewing the pslist output, the suspicious processes found were MEMYUoYU.exe (PID 6444), ceIcEMkw.exe (PID 1236)
1 | Give the PID of the displayed suspicious processes (do not consider does already analysed, neither their sons). If more than one put a comma (e.g. 1, 2) |
Step 5: Finding the Directory of the Malicious Processes
Using filescan, I determined the file locations:
1 | $ python3 vol.py -f ~/Downloads/capture_ram.elf windows.filescan | grep -i "MEMYUoYU.exe" |
Let’s submit the output in the specified format:
1 | What is the directory of the file related to process 6444? Give the complete path from the root directory to the extension. (e.g. C:\path\my\process.extension)C:\Users\User\kOIUsMQU\MEMYUoYU.exe |
Step 6: Finding the Directory of Another Malicious Process
I am not sure why the author wanted us to repeat the same step again, but let’s proceed.
1 | What is the directory of the file related to process 1236? Give the complete path from the root directory to the extension. (e.g. C:\path\my\process.extension)C:\ProgramData\hwQkYMwk\ceIcEMkw.exe |
Step 7: Identifying the Parent PID of Malicious Processes
By checking the PPID of these processes, I found:
Parent PID: 4680
1 | What is the parent PID of the malicious processes? |
Step 8: Finding the number of encrypted files
To determine this, I first searched for keywords like crypt in the windows.filescan output of Volatility but didn’t find any significant leads. Since malware was involved, I then tried the windows.malfind plugin, which revealed some useful information:
1 | $ python3 vol.py -f ~/Downloads/capture_ram.elf windows.malfind |
Following this, I searched for the file in filescan, retrieved the virtual address, and dumped the file using the windows.dumpfiles plugin. Upon checking its contents, I found a list of 288 encrypted files.
1 | How many files have been encrypted? |
Step 9: Identifying the filename containing the list
I know it is ZcgU.txt
1 | Give the filename of the file containing the list of the files to be encrypted. (only the filename not the whole path). |
Step 10: Finding the cryptocurrency
The malfind output above shows that Bitcoin was used.
1 | Which cryptocurrency is used? |
Step 11: Identifying the GET Request
To answer this, I searched for GET requests in the memory file. I compared them which were looking similar to those in the PCAP but found no match. However, I had also discovered a GET request during the malfind search, which turned out to be the missing one:
1 | Which GET request is not present in the pcap? Give the whole request (METHOD resource, e.g. POST /accessed/resource) |
Step 12: Finding the reason for the fine
The question was a bit confusing, so I explored various Volatility plugins. Eventually, I dumped the memory of the malware process MEMYUoYU.exe and searched for related strings:
1 | $ python3 vol.py -f ~/Downloads/capture_ram.elf windows.memmap --pid 6444 --dump |
This revealed the following text:
1 | imits:P |
Thus, the answer is “unauthorized or pirated software”.
1 | Why did you have to pay a fine? |
Step 13: Findint the amount of fine
From the extracted text, the fine amount is clearly stated as $250,000.
1 | What is the amount of fine? (e.g. €10,000) |
Step 14: Searching for the forum
Searching in PID 6444 didn’t provide an answer, so I checked the memory dump of PID 1236. By analysing it with strings command, I can find some questions on reddit.com site.
1 | Which forum is used to ask for BitCoin AMT? |
Step 15: Finding the BitCoin address
To find the address, I searched for charts01.bitcoincharts.com.
1 | $ strings -el pid.1236.dmp | grep -iC5 "charts01.bitcoincharts.com" |
I got the address as 1yQBzAaZx7FojqMmTtHPTfZ42T4t6Q1Uh.
1 | What is the BitCoin address at charts01.bitcoincharts.com? |
Step 16: Identifying the directory
If I search with the help of strings and grep the \Desktop\ , you can found multiple references to \Users\User\Desktop\ch2\ as shown below:
1 | $ strings -el pid.6444.dmp | grep -i "\\\DESKTOP" |
Secondly I can also get the same directory with the help of windows.handles plugin, so the answer was ch2.
1 | From which directory does process 6444 come from? Give only the local path with directory name (NOT the absolute path, i.e. without Desktop, e.g. mydirectory) |
Step 17: Getting the filename of the process
Since the above output had the executable with a long string name, which was also mentioned in the PID 1236 process, I checked that and it turned out to be the desired one.
1 | What is the filename of the process which executed the two malware with PID 4680? Give only the filename with extension (e.g. myfile.ext) |
Hooray I got our flag.
Flag:
1 | srdnlen{DFIR3:Windows_RAMsomware} |
DFIR 4 - MalThrInt
Challenge Description
We have been notified of an attack in one of our machines. This is a real forensics investigation and you have to retrieve Threat Intelligence data from VirusTotal using the last answered hash of DFIR-3-RAMsomwhere and answer to the related questions. At the end you will get the flag when you answer everything correct.
NOTE: This is a real malware. Do not execute nothing. Pay attention and be careful. Srdnlen denies every damage on your infrastructure.
This is a remote challenge, you can connect to the service with: nc dfir4.challs.srdnlen.it 1987
Author: slsanna
Solution
This challenge required retrieving Threat Intelligence data from VirusTotal using the last answered hash from DFIR-3-RAMsomwhere.
First, search for the hash 0002bdf0923262600d3ef66d1ec6b2396a434e6f7626a9d70241a5663ee2f736 on the VirusTotal website to gather the necessary information. Then, start interacting with the provided nc instance.
1 | $ nc dfir4.challs.srdnlen.it 1987 |
Step 1: VT Detection Score
The currently VirusTotal detection score is 65/72. While it may change over time, the correct answer here is 62/72. If you face issues, you can attempt a brute-force approach by testing nearby values.
1 | What is the VT detection score? |
Step 2: Popular Threat Label
Navigate to the Detection page under the Dynamic Analysis Sandbox Detections section. The correct answer is:
1 | Give the popular threat label |
Step 3: Target Machine
On the Details page, scroll down to find the target machine information. The answer is:
1 | What is the target machine? |
I got tricked by this question. At first, I tried using the DLLs mentioned in the Files Opened and Runtime Modules sections, but there were many, and I failed to find the correct ones. Then, I checked the Imports section on the Details page, where I found two DLL modules. After trying those, I got the desired result.
1 | Which dlls are used? Give just the name without .dll extension. If more than one put a comma (e.g. 1, 2) |
Step 5: Malicious IP Address
On the Relations page, look under the Contacted IP addresses section. 1 IP is detected and got the desired result:
1 | What is the malicious IP address? |
Step 6: Registrar of the Domain
Under the Contacted Domains section, identify the domain related to the previous Bitcoin address.
1 | What is the registrar of the domain related to the previous bitcoin address? |
Step 7: MITRE Persistence Techniques
On the Behavior page, check the MITRE ATT&CK Tactics and Techniques section. Similarly you will get the answer for the Step - 8, 9, 10.
1 | Which persistence techniques according to MITRE does it have? If more than one put a comma (e.g. 1, 2) |
Flag:
1 | srdnlen{DFIR4:VirusTotal4PPID_ThreatIntelligence} |

